Advanced configuration
Running Jenkins with an insecure Docker registry
For testing purposes, you can configure an insecure Docker registry. To enable an insecure registry, pass in the –insecure-registry option to the Docker daemon that runs on each Jenkins agent.
The instructions below will show you how to use this option with the jenkins-dind image that is configured by default when you install the Jenkins service.
Configuring Docker daemon
- Get the hostname and port of your Docker registry. For example, if you're using the Artifactory package for DC/OS, it'll look something like:
artifactory-lb.marathon.mesos:5001
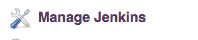
Navigate to "Manage Jenkins".
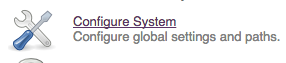
Navigate to "Configure System".
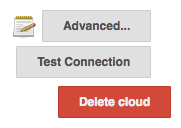
Scroll to the "Mesos Cloud" section and click on "Advanced...".
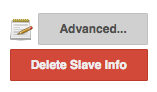
Under the default label (defined with an empty label string), click "Advanced...".
Find the "Parameters" section and create a new parameter.
Set the "Name" to
envand the "Value" toDOCKER_EXTRA_OPTS=--insecure-registry artifactory-lb.marathon.mesos:5001, using the hostname of your insecure registry.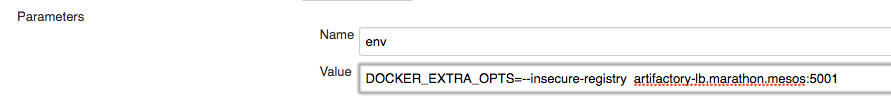
Using this registry in a job
To use this registry in a job, simply prefix its hostname when using the Docker command line, as normal. For example:
#!/bin/bash
docker login -u myuser -p mypassword -e my@email.com artifactory-lb.marathon.mesos:5001
docker build -t artifactory-lb.marathon.mesos:5001/myimage:mytag .
docker push artifactory-lb.marathon.mesos:5001/myimage:mytag
 Jenkins Documentation
Jenkins Documentation