You can implement fine-grained user access to jobs by using either the DC/OS UI, the CLI or the API. The Metronome permissions allow you to restrict a user’s access to jobs on either a per job or a per job group basis. This section walks you through the steps to accomplish this.
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
- A user account to assign permissions to.
Via the DC/OS UI
-
Log into the DC/OS UI as a user with the
superuserpermission.
Figure 1. DC/OS UI login
-
Select Organization and choose Users or Groups.
-
Select the name of the user or group to grant the permission to.
Figure 2. Choose user or group to add permissions to
-
From the Permissions tab, click ADD PERMISSION.
-
Click INSERT PERMISSION STRING to toggle the dialog.
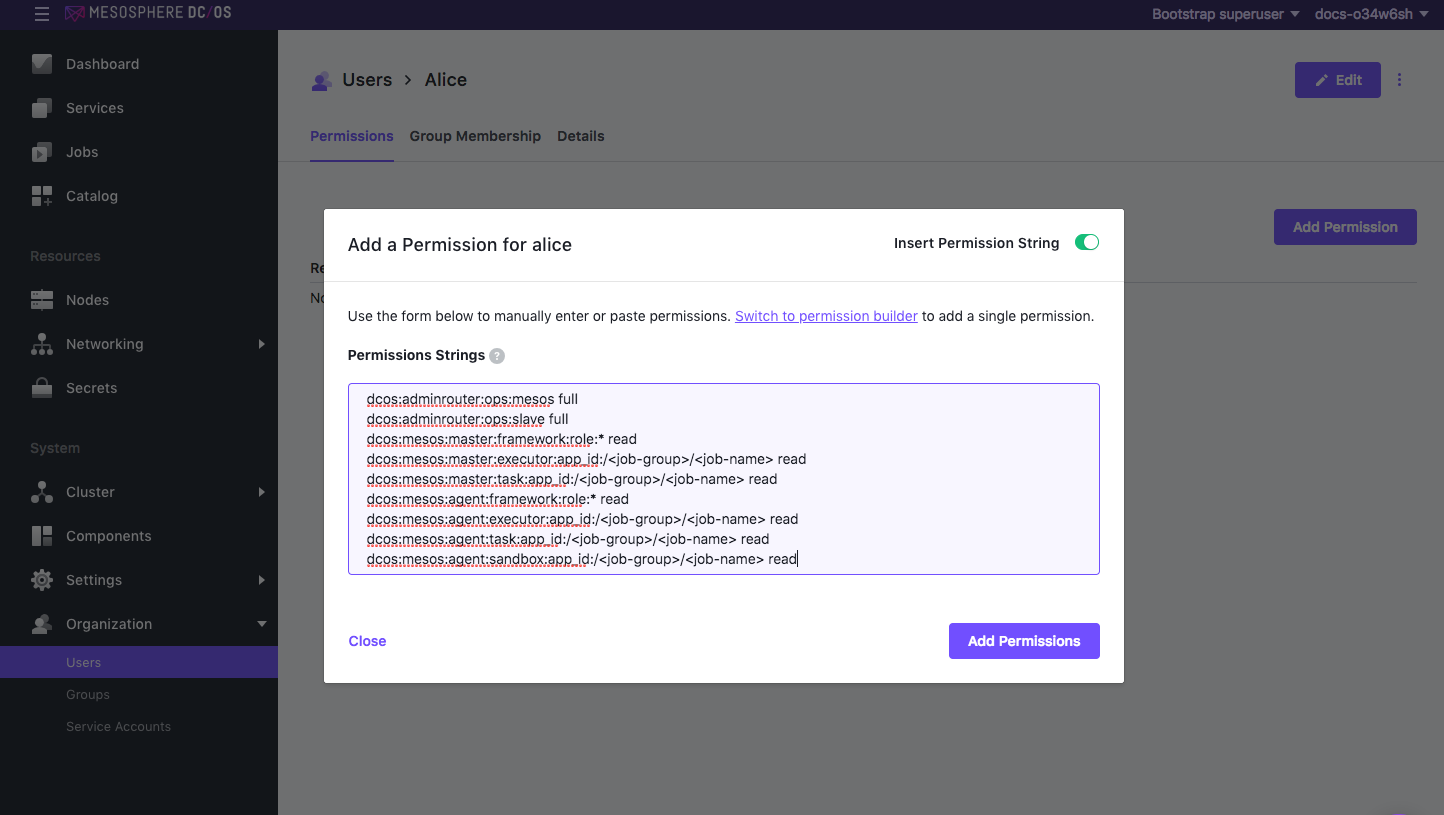
Figure 3. Add permissions
-
Copy and paste the permission in the Permissions Strings field. Choose the permission strings based on your security mode.
Permissive
-
DC/OS jobs access:
Specify your job group (
<job-group>), job name (<job-name>), and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:metronome:metronome:jobs:<job-group>/<job-name> read,update.dcos:adminrouter:service:metronome full dcos:service:metronome:metronome:jobs:<job-group>/<job-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full
Strict
-
DC/OS jobs access:
Specify your job group (
<job-group>), job name (<job-name>), and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:metronome:metronome:jobs:<job-group>/<job-name> read,update.dcos:adminrouter:service:metronome full dcos:service:metronome:metronome:jobs:<job-group>/<job-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full dcos:mesos:master:framework:role:* read dcos:mesos:master:executor:app_id:/<job-group>/<job-name> read dcos:mesos:master:task:app_id:/<job-group>/<job-name> read dcos:mesos:agent:framework:role:* read dcos:mesos:agent:executor:app_id:/<job-group>/<job-name> read dcos:mesos:agent:task:app_id:/<job-group>/<job-name> read dcos:mesos:agent:sandbox:app_id:/<job-group>/<job-name> read
-
-
Click ADD PERMISSIONS and then Close.
Via the CLI
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
Tips:
- To grant permissions to a group instead of a user, replace
users grant <user-name>withgroups grant <gid>.
Permissive
-
DC/OS jobs access:
-
Grant the permission to job group (
<job-group>) and job name (<job-name>).dcos security org users grant <user-name> adminrouter:service:metronome full --description "Controls access to Metronome services" dcos security org users grant <user-name> service:metronome:metronome:jobs:<job-group>/<job-name> full --description "Controls access to <job-group>/<job-name>"
-
-
DC/OS service tasks and logs:
-
Grant the permission to a user (
<user-name>).dcos security org users grant <user-name> adminrouter:ops:mesos full --description "Grants access to the Mesos master API/UI and task details" dcos security org users grant <user-name> adminrouter:ops:slave full --description "Grants access to the Mesos agent API/UI and task details such as logs"
-
Strict
-
DC/OS jobs access:
-
Grant the permission to job group (
<job-group>) and job name (<job-name>).dcos security org users grant <user-name> adminrouter:service:metronome full --description "Controls access to Metronome services" dcos security org users grant <user-name> service:metronome:metronome:jobs:<job-group>/<job-name> full --description "Controls access to <job-group>/<job-name>"
-
-
DC/OS service tasks and logs:
-
Grant the permission to the user (
<user-name>) and group (<job-group>).dcos security org users grant <user-name> adminrouter:ops:mesos full --description "Grants access to the Mesos master API/UI and task details" dcos security org users grant <user-name> adminrouter:ops:slave full --description "Grants access to the Mesos agent API/UI and task details such as logs" dcos security org users grant <user-name> mesos:master:framework:role:* read --description "Controls access to frameworks registered with the Mesos default role" dcos security org users grant <user-name> mesos:master:executor:app_id:/<job-group>/<job-name> read --description "Controls access to executors running inside <job-group>/<job-name>" dcos security org users grant <user-name> mesos:master:task:app_id:/<job-group>/<job-name> read --description "Controls access to tasks running inside <job-group>/<job-name>" dcos security org users grant <user-name> mesos:agent:framework:role:* read --description "Controls access to information about frameworks registered under the Mesos default role" dcos security org users grant <user-name> mesos:agent:executor:app_id:/<job-group>/<job-name> read --description "Controls access to executors running inside <job-group>/<job-name>" dcos security org users grant <user-name> mesos:agent:task:app_id:/<job-group>/<job-name> read --description "Controls access to tasks running inside <job-group>/<job-name>" dcos security org users grant <user-name> mesos:agent:sandbox:app_id:/<gid>/ read --description "Controls access to the sandboxes of <job-group>/<job-name>"
-
 DC/OS Documentation
DC/OS Documentation